Physical Security +
Logical Security +
Obfuscation Engine =
Pinnacle of Privacy
Introducing the Arpir Secure Laptop

Physical Security meets Logical Security
Secure. Private. Uncompromised.
The Arpir Secure Laptop, equipped with the Qubes operating system, is engineered to safeguard sensitive data. By compartmentalizing applications, it significantly minimizes the risk of data breaches, isolating incidents to individual segments.
Upon startup, the laptop operates in a decoy OS mode, presenting a standard interface to deter unauthorized access, while the secure Qubes environment remains hidden for confidential work.
This device employs layered networks to secure internet connections, ensuring all online activities remain private and untraceable. For the highest level of security, it also offers a feature to open files in a completely internet-isolated environment, preventing any potential data leakage.
How it works:
Keep separate, stay secure
Arpir Secure Laptop
Advanced Protection with Killswitch Functionality
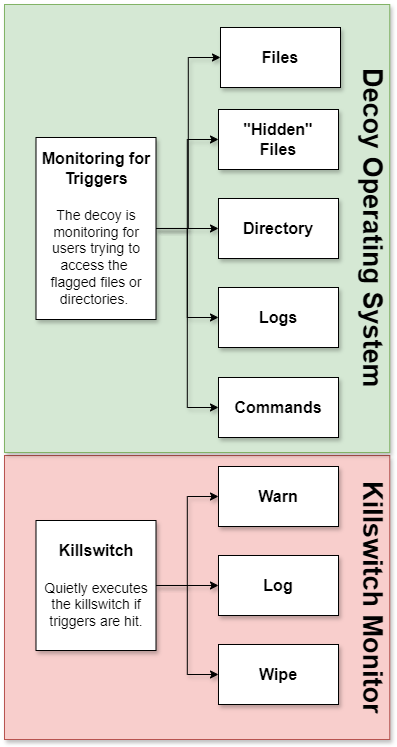
The Arpir Secure Laptop includes a sophisticated killswitch feature that allows users to designate a specific file as a trigger. If this file is accessed, it activates the killswitch, instantly wiping the secure drive to prevent unauthorized data access. This feature is essential for protecting sensitive information if the laptop is lost or stolen, and also offers a discreet way to erase data by simply opening the file.
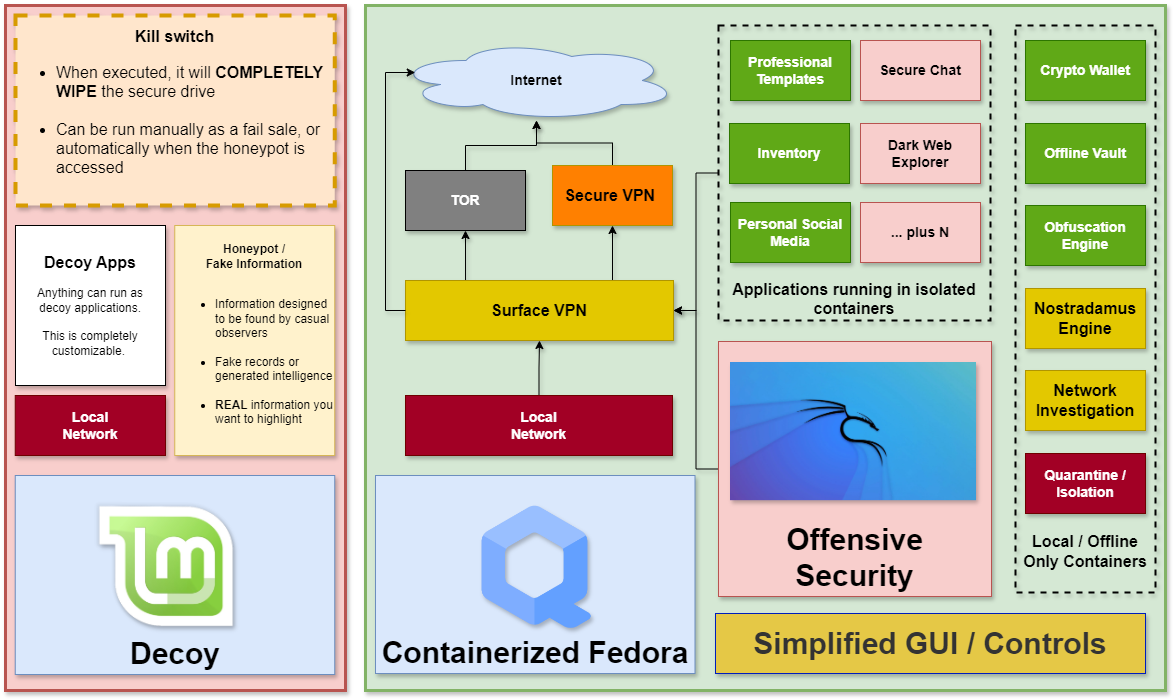
The Arpir Secure Laptop’s killswitch feature offers robust protection by enabling the immediate and discreet wiping of the secure drive when a designated trigger file is accessed, safeguarding sensitive information in the event of loss or unauthorized access.
Introducing Arpir
Decoy OS and Killswitch
The Arpir Secure Laptop features a cleverly designed dual-operating system to maximize security and privacy. At the forefront is a top-level decoy operating system powered by Linux Mint, which functions as a typical OS for everyday tasks like web browsing. This system is designed to deflect any casual investigation, presenting itself as a normal laptop with no indication of the sophisticated secure environment operating beneath. Users are encouraged to utilize this decoy system for routine activities, ensuring that the secure layers remain discreet and undetected.
The Arpir Secure Laptop is equipped with an innovative killswitch feature, designed to enhance security when physical control over the device is compromised. Users can configure a specific file within the operating system that, when accessed, activates the killswitch. This triggers an immediate wipe of the secure drive, effectively removing sensitive information to prevent unauthorized access. This functionality is not only crucial for situations where the laptop is lost or stolen, but it also allows for a discreet method to erase data simply by opening the designated file.
Additionally, the system supports stacking network layers, allowing you to build secure connections atop one another. This layered approach is designed with a fail-close mechanism, ensuring that in the event of a disruption, accidental exposure is prevented by automatically severing the connections.
Built on the most secure platorm
Powered by Qubes OS
The Arpir Secure Laptop’s operating system is powered by Qubes, famously utilized by Edward Snowden for its robust security features. It enhances data protection through the use of secure containers that operate independently, unable to see or interact with each other, thereby preventing mutual compromise.
Reasonably Secure
Qubes OS, which powers the Arpir Secure Laptop, is widely regarded as a “reasonably secure” operating system due to its unique approach to security by isolation. It prides itself on this classification because it acknowledges the practical limits of security in today’s complex computing environments, while striving to provide the best possible protection against threats.
By compartmentalizing applications, data, and processes into separate virtual machines, Qubes ensures that the compromise of one area does not jeopardize the integrity of others, thus maintaining a high level of security that adapts to the needs and threats faced by modern users.
Docker Integration
The Arpir Secure Laptop fully integrates Docker, enabling the effortless running of powerful software applications without the need for manual configuration.

Linux Mint for top layer OS
The Arpir Secure Laptop utilizes Linux Mint as its top-level operating system, chosen for its powerful capabilities and user-friendly interface that many are already familiar with.

Offensive Security with Kali Linux
The Arpir Secure Laptop integrates with Kali Linux to provide users with a comprehensive suite of powerful offensive security tools, all curated and maintained within a reliable package for advanced penetration testing and security assessments.
Secure Your Digital Wealth
Integrated Crypto and Credential Vaults for Ultimate Security
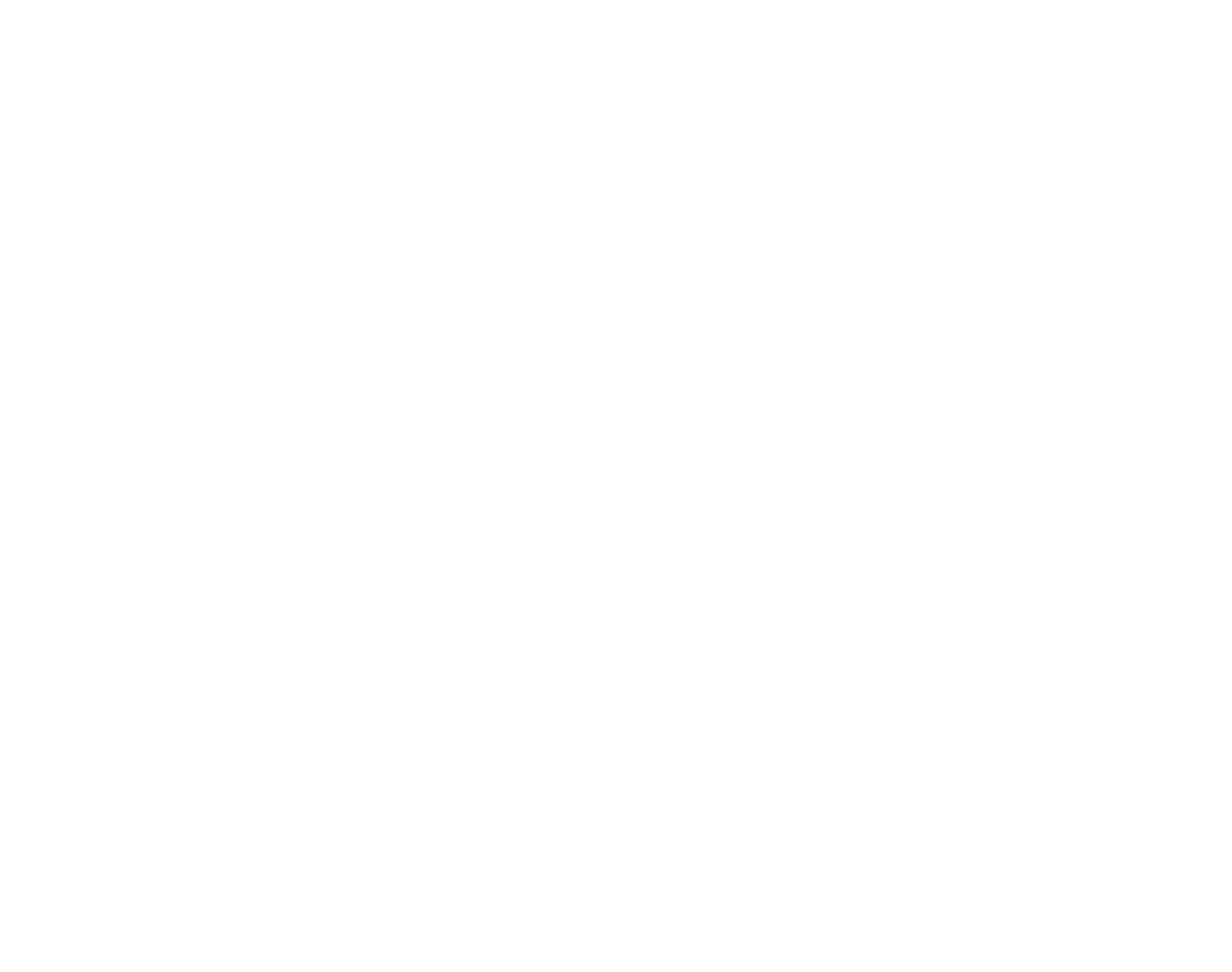
Dedicated Crypto Vaults.
These are secure containers specifically preconfigured with cryptocurrency wallets, designed to manage and store your digital currencies efficiently. The integration ensures that your assets are not only organized but also guarded within a robust security framework.
Enhanced Trust with Multisignature Wallet Support
Dedicated Crypto Vaults
The combination of crypto and credential vaults on the Arpir Secure Laptop makes it a formidable tool for anyone invested in the security and management of digital currencies. This dual-vault system not only organizes your assets but also fortifies them against external threats, making it an essential device for modern digital transactions.
Trust but Verify
Multi-Signature Wallets
The Arpir Secure Laptop takes cryptocurrency security to the next level with support for multisignature wallets. These advanced wallets require multiple keys to authorize a transaction, making it impossible for funds to be transferred without the agreement of all parties involved. This feature is ideal for establishing trust in transactions, allowing one party to verify that funds are present while ensuring they cannot be moved unilaterally.
What multi-signature means
Multi-signature wallets for cryptocurrency add an extra layer of security by requiring two or more keys to authorize a transaction, thus preventing any single individual from unilaterally accessing the funds.
Each key is held by a different party, and a transaction can only be executed when the specified number of signatories agree and use their keys, making it an ideal solution for enhancing trust among business partners or in scenarios requiring collective decision-making.
This mechanism not only safeguards against theft or unauthorized access but also provides a transparent method for managing and securing large or critical transfers of digital currencies.
Multisignature wallets are particularly useful in business relationships or collaborations where trust needs to be built and financial assurances are necessary. By enabling one party to confirm the availability of funds and the other to fulfill obligations knowing payment is secured, multisignature wallets streamline the process of verifying work completion and releasing funds. This system not only enhances security but also fosters a more trustworthy and reliable partnership.
Robust isolation for safety
Completely Offline Wallets
What sets the credential vault apart is its complete isolation from any network or internet access. This design decision ensures that your passwords remain protected from online threats, providing a secure environment that is impervious to hacking or unauthorized access. The isolation maximizes the safeguarding of your credentials, keeping them accessible only to you, under the strictest privacy conditions.
Bitcoin
Support for multi-signature wallets
Monero
Crypto currency built for privacy
Etherium
A global standard
Offline crypto vaults on the Arpir Secure Laptop provide unbeatable security for your digital assets by ensuring that your cryptocurrency and keys are stored in an environment completely isolated from online threats.
Logical Security

The Nostradamus Engine
Obfuscation and Encryption Engine
The obfuscation engine on the Arpir Secure Laptop serves as a sophisticated security measure designed to protect user data by generating and interspersing fake data among genuine information. This system effectively confuses and misleads potential intruders by making it extremely challenging to discern real data from decoys.
The goal of this engine is to “poison the well,” rendering all information on the laptop unreliable and unusable to anyone who unlawfully gains access to the device. This advanced approach not only secures data against unauthorized extraction but also adds an extra layer of privacy protection by obscuring the user’s actual activities and data.
Data Segmentation:
Anonymity and privacy assured
How Obfuscation works
The problem with Checkov’s Gun
The Arpir Secure Laptop features a groundbreaking security component known as the Nostradamus Engine, designed to protect your information if the device is ever compromised. This innovative obfuscation engine functions by generating fake data that closely resembles your actual data, effectively blurring the line between the real and the counterfeit. The primary goal is to protect the integrity of your information by making it impossible for an adversary to distinguish genuine data from fabrications.
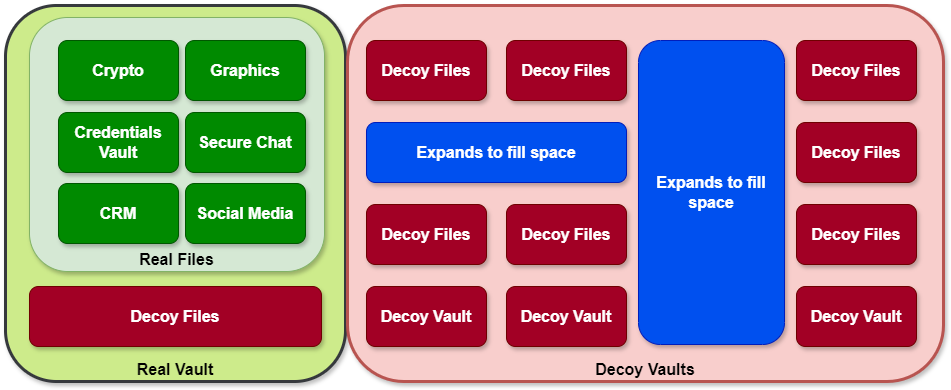
The Arpir Secure Laptop’s secure container design and integrated obfuscation engine ensure that each application runs in isolated, encrypted environments, providing unmatched data protection and privacy, regardless of usage.
Disguise and Protect
Shield your data if compromised
In the event that the laptop falls into the wrong hands, either accidentally or through deliberate targeting, the Nostradamus Engine acts to “poison the well,” rendering all stored data suspect. This mechanism ensures that no piece of data on the laptop can be reliably assumed to be true, providing a robust layer of defense against data theft or misuse. By deploying such obfuscation techniques, the Arpir Secure Laptop safeguards your digital assets, making unauthorized access fundamentally useless.
Our obfuscation engine employs a sophisticated array of stacked ciphers and esoteric coding techniques to create an incredibly complex security layer, designed for scenarios where utmost confidentiality and protection are matters of life or death.
NOT AI Enabled
The Arpir Secure Laptop emphasizes the importance of robust offline security solutions, deliberately choosing not to incorporate AI technologies in its design.
This approach is rooted in a commitment to minimizing potential vulnerabilities that could arise from online connections and the complexities of AI systems. By focusing on offline capabilities, the laptop ensures that its security mechanisms remain straightforward and highly controllable, reducing the risk of breaches and maintaining a high standard of data protection.
This strategy is particularly effective for users who prioritize a secure, predictable computing environment free from the unpredictability and potential exploits associated with AI-driven features.
Secure Container Design
Depth in defense mechanisms
The Arpir Secure Laptop boasts a highly secure container design that isolates applications from one another, ensuring that activities conducted on one part of the system have no impact on others.

Globally Unique
3 types of Obfusction Engines
The Arpir Secure Laptop offers three distinct types of obfuscation engines, each providing varying capabilities and levels of protection to meet diverse security needs and preferences.

Core Obfuscation Engine
Built on randomization
Encfs: Reasonably Secure
EncFS (Encrypted File System) is a user-friendly file encryption system that provides a reasonably secure environment for storing sensitive data.
While EncFS is generally reliable, it does present certain trade-offs, particularly when different versions of the same data are exposed. This exposure could potentially allow for some forms of cryptographic analysis, but EncFS includes safeguards to mitigate these risks effectively.
One of the robust features of EncFS is its ability to maintain the indistinguishability between modified decoy files and legitimate ones, greatly complicating any attempts to derive conclusions from the data.
This feature ensures that even if security breaches occur, the confusion sown by these indistinguishable files significantly enhances the overall security of the stored data.
The core Arpir obfuscation engine is designed around principles of randomization and disrupting logical connections between files and their ownership to enhance security and anonymity.

Business Records Obfuscation
Builds fake data to mirror your own
Ixnar, an obfuscation engine tailored for business and trade records, generates convincing fake data that mirrors actual data, effectively concealing real information to prevent unauthorized parties from discerning the truth.

Full comprehensive engine
The most secure engine for extreme security
The Nostradamus engine employs a sophisticated array of stacked ciphers and esoteric coding techniques to create an incredibly complex security layer, designed for scenarios where utmost confidentiality and protection are matters of life or death.
Network Security

Multiple Stacked Networks
Advanced VPN and TOR Integration
The Arpir Secure Laptop encourages the use of VPNs to maintain consistent and secure online activity across all devices. It is optimized for seamless integration with any mainstream VPN service, encouraging users to establish a basic VPN connection that remains active at all times.
This initial layer of VPN, intended for use across various platforms, helps standardize your digital footprint, making your online activities indistinguishable from other users of the same VPN. This strategy not only masks your activity from your internet service provider but also lays the groundwork for more secure, layered connections.
Stacked Network Design:
Secure, Private, and Anonymous Internet Access
Introducing Hehge
Ironclad Communication Security
Beyond the surface-level VPN, the Arpir Secure Laptop supports a more secure VPN layer, which should be purchased anonymously using cryptocurrency to ensure no identifiable information is linked to the account.
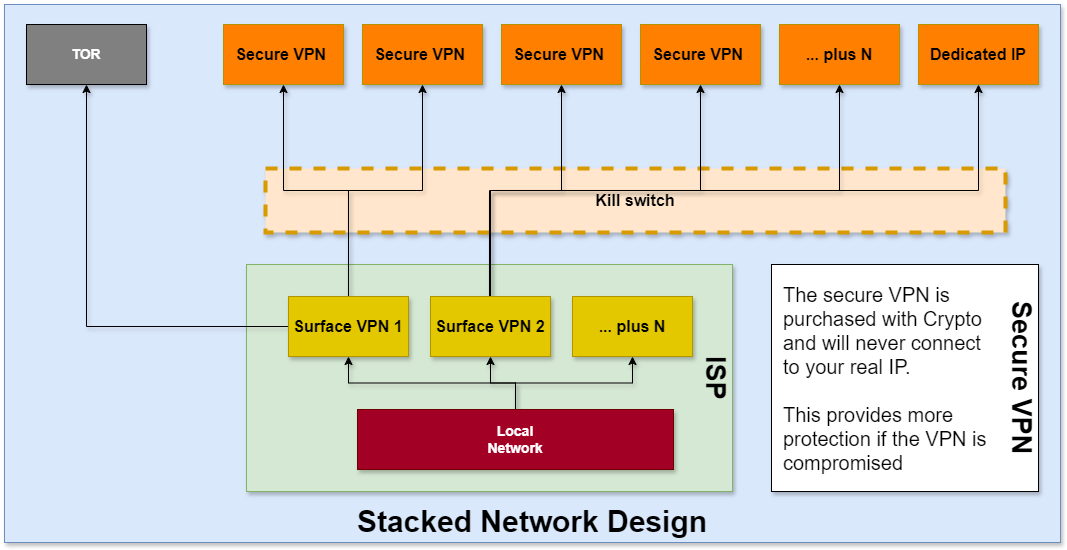
This secondary VPN allows for multiple simultaneous connections and can be compartmentalized to assign specific, secure IP addresses to individual container apps within the system. For enhanced security, users can insert a TOR layer between these VPN connections, effectively anonymizing activity beyond the visibility of ISPs. The system also supports specialized TOR-optimized browsers that operate over the VPN, maintaining privacy with one-time-use disposable containers for ultimate data protection.
Browse with confidence
Secure Dark Web Access
The Arpir Secure Laptop enhances your online anonymity with optimized TOR layers, which are built to function seamlessly atop the established VPN layer. This configuration allows users to operate TOR without any visibility from their Internet Service Provider (ISP), ensuring that all online activities remain private and untraceable. The integration of TOR over VPN adds an extra layer of security, as the encrypted VPN connection hides TOR usage from your ISP, reinforcing your digital privacy.
Additionally, the laptop features completely anonymous, one-time-use disposable containers. These containers are ideal for sessions requiring the utmost confidentiality, as they are destroyed after a single use, leaving no trace of user activity. This feature is particularly beneficial for sensitive tasks, providing an extra layer of security by ensuring that no residual data is left behind that could compromise user privacy.
Establishing a secure setup with robust privacy protections and layered security measures is essential before accessing the dark web to safeguard your identity and maintain confidentiality in your online interactions.
Failsafe network connections
Stacked Communication Layers
The Arpir Secure Laptop employs a sophisticated stacked communication layer approach to enhance network and internet security, providing robust protection for user data during online activities. This design consists of multiple layers of communication protocols, each operating independently.
The primary advantage of this stacked approach is that it adds depth to the security framework, as each layer functions as a distinct barrier, complicating potential unauthorized access. This architecture is particularly beneficial in preventing data leaks or breaches, as the failure of one layer does not compromise the integrity or confidentiality of the entire system.
Moreover, the stacked design of the laptop’s communication layers is engineered to be fail-closed, which means that if a single layer encounters a failure, it automatically shuts down without exposing the data from other layers or compromising the overall security. This fail-closed mechanism ensures that the user’s data remains protected and that the integrity of the network connection is maintained, even in the event of partial system failures.
This not only shields the data from potential intruders but also maintains the anonymity and security of the user’s activities, making it an essential feature for those requiring high levels of security in their internet and network interactions.
Hardware


The Dissident
Empowering non-technical populations for advanced offensive cyber warfare
Introducing the Dissident, a custom cybersecurity platform tailored to support any global operation. Expanding on the Skeleton Key’s capabilities, the Dissident provides users with a plug-and-play tool that enables secure communication with any system worldwide, without leaving a trace.
Additionally, it comes equipped with a variety of pre-configured offensive security and information-gathering tools, making advanced technical knowledge unnecessary. Experience the power and convenience of the Dissident for all your cybersecurity needs.